Setting up Linux to use ssh key for logins
|
Menu
|
This page is work in progress currently
We will cover both setup of a login just using ssh public/private key pair. Using a key pair is much more convenient. If you combine a key pair with a passphrase you will get a much more secure login. Caution: Protect your private key! Think of the public key as the lock on your house and the private key as the key on your keychain to get in. If someone else gets hold of your private key they can log into your house (server). If you have used, or plan to use any Linux servers in AWS they use key pairs to be able to log into the system. They will ask you to create a new key when you first make the first machine. You will download the private key. They will not store the private key, so you get one shot at downloading it. They will keep a copy of the public key to put on any additional servers you want to use the same key on. There is no serious issue using the same key on multiple servers (as long as you keep the private key safe). If you want to use the private key AWS created with PuTTY on Windows you will need to change its format. This tutorial has steps on how to change formats for the private key file. Sometimes you might get a new account on a server where someone else created your key pair. You are hoping they did not keep a copy of the private key. You can use these steps to create a new key pair and replace the one that they set up. You can also use these steps if you think your private key has been compromised. |
Creating your key pair with PuTTY
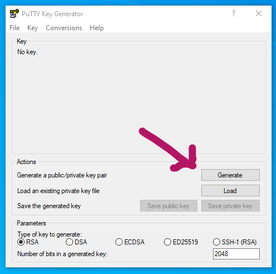
Most people use Windows as their primary workstation. The top choice for ssh terminal emulation on Windows is PuTTY. The PuTTY software suite includes a tool for creating key pairs called PuTTYgen. The tool is pretty intuitive. Once you open it you will see several buttons. One of them is the Generate button. Click on this button to start the process of generating the key. You will see a progress bar across the top. It will also ask you to move the mouse pointer around inside the grey window under the progress bar. This is to generate randomness to create a stronger key. Computers are actually pretty bad at generating randomness. So PuTTYgen is simply asking you to help create randomness.
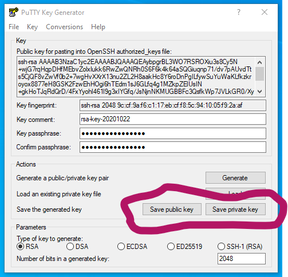
Once the key is generated then you will need to save both the public key and the private key. PuTTYkeygen gives you buttons for saving each key file. Save the private key file and store it in a safe location on your computer. If you don't put a key passphrase in you will get a warning (see below about using key passphrases) asking if you really want to save without a key passphrase.
Save the public key file with a .pub extension. This is the file that needs to go on the Linux servers you will log into. If someone else is setting up the access to the servers then you will simply send them the public key to apply to your account on the servers. If you are setting up the server to use key pairs instead of a username/password authentication then you will put the public key on the server in your home drive. Typically the file goes into the ~/.ssh/ folder. Usually it goes into a file called authorized_keys. If you don't have that file just copy your .pub file to that name in that folder. Then set the rights using chmod 600 ~/.ssh/authorized_keys on the file.
Save the public key file with a .pub extension. This is the file that needs to go on the Linux servers you will log into. If someone else is setting up the access to the servers then you will simply send them the public key to apply to your account on the servers. If you are setting up the server to use key pairs instead of a username/password authentication then you will put the public key on the server in your home drive. Typically the file goes into the ~/.ssh/ folder. Usually it goes into a file called authorized_keys. If you don't have that file just copy your .pub file to that name in that folder. Then set the rights using chmod 600 ~/.ssh/authorized_keys on the file.
Key Passphrase
It is possible to put a passphrase on a private key file. That way if someone gets hold of your private key file they need to also know the passphrase to be able to use it on the login. The passphrase gets saved in the private key file. If you have private key files that currently don't have a passphrase you can add one in by simply loading your private key file into PuTTYkeygen add a passphrase and save it again. Then get rid of the private key file without the passphrase.
Caution: if someone else gets hold of your private key file and knows the passphrase then changing it after the fact will not fix the issue. At that point create a new key pair and implement it and take out the old public key from your servers!
The primary benefit of a passphrase is if someone gets hold of your private key file they cannot use it unless they also know the passphrase. So it is extremely important to make your passphrase strong. This does not mean it has to be some cryptic phrase like A8to$42*loiEn# or other crazy string. Your best bet is something that is easy for you to remember and type, and that it is fairly long. Ideally you want something that is at least 15 characters or longer that includes upper and lower case characters. Think of a good phrase that you can remember. A good example of a solid passphrase is SnoopyHalloweenHolidayCoffeeMug. It is long (30 characters), has a mix of case for the letters, and very difficult to brute force crack. It also has the benefit of being easy to remember, and to type. How did I come up with that you might ask? I looked around my desk for something and, yes you guessed it, there was a Snoopy holiday mug with my coffee in it.
There is no way for a corporate or server policy to enforce complexity, so it will be fully on you to create a good passphrase. If you use a easy to remember and type passphrase then it will not feel so burdensome to have a strong passphrase.
Caution: if someone else gets hold of your private key file and knows the passphrase then changing it after the fact will not fix the issue. At that point create a new key pair and implement it and take out the old public key from your servers!
The primary benefit of a passphrase is if someone gets hold of your private key file they cannot use it unless they also know the passphrase. So it is extremely important to make your passphrase strong. This does not mean it has to be some cryptic phrase like A8to$42*loiEn# or other crazy string. Your best bet is something that is easy for you to remember and type, and that it is fairly long. Ideally you want something that is at least 15 characters or longer that includes upper and lower case characters. Think of a good phrase that you can remember. A good example of a solid passphrase is SnoopyHalloweenHolidayCoffeeMug. It is long (30 characters), has a mix of case for the letters, and very difficult to brute force crack. It also has the benefit of being easy to remember, and to type. How did I come up with that you might ask? I looked around my desk for something and, yes you guessed it, there was a Snoopy holiday mug with my coffee in it.
There is no way for a corporate or server policy to enforce complexity, so it will be fully on you to create a good passphrase. If you use a easy to remember and type passphrase then it will not feel so burdensome to have a strong passphrase.
Creating key on Linux
We will be using a command line tool on Linux to create the key pair.
Adding public key to Linux server
Once you get the key pair created you will need to add your public key to any Linux servers that you want to log into with that key pair.
Converting private key format
Depending on where you make the key pair you might have to change the format of the private key to work properly. Typically this situation happens when you make the key pair on Linux and then want to use the private key on Windows in PuTTY.
Using key in PuTTY
Now that you have the key pair created we need to look at how to set it up in PuTTY. I am only touching on PuTTY because it is the most commonly used Windows ssh emulator. Other programs will use some similar process.
Home |
About |
Services |
Copyright © 2016